Meltdown and Spectre attack
- Inicie sesión o regístrese para enviar comentarios
Hi to everyone!
I did notice with Hardinfo that my cpu is affected by a Meltdown and Spectre attack, see picture. What is possible doing in order to face this problem? Thanks for the attention. Regards
| Adjunto | Tamaño |
|---|---|
| IMG_HardwareInfos.jpg | 1.68 MB |
Aren't all meltdown and spectre attacks merely theoretical? I don't think I've ever heard of an actual exploit in the wild that can take advantage of those theoretical vulnerabilities.
I encourage reading this:
https://www.fsfla.org/ikiwiki/blogs/lxo/pub/who-is-afraid-of-spectre-and-meltdown.en.html
That article makes for dangerous advice. Any unmitigated vulnerability allows other vulnerabilities to compound, and even the most careful of computer users is exposed to some vectors of attack. Every data file parsed and loaded into memory can exploit vulnerabilities in the program doing the parsing. Every server receives requests that must be parsed and some execution must be done to provide an answer to the client. There are countless examples of exploits that have affected key free programs, and meltdown/spectre provides ways to escalate them towards full-on control of the attacked machine.
"We have no reason to fear Spectre, Meltdown or similar side channels when we do our computing using only trustworthy Free Software[...]"
How do you know which of your free software is trustworthy in terms of security? Just because the licensing is trustworthy does not mean that you don't need to secure your systems. Advocating for disabling the free software mitigations because they reduce performance is reckless. Pointing out that all of our software can be audited only dismisses the problem.
--
To answer the initial question (What is possible doing in order to face this problem?), all existing free software mitigations are included in Trisquel, here is some information from upstream sources:
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown/
https://wiki.debian.org/DebianSecurity/SpectreMeltdown
Some key takeaways:
* There is no mitigation for Meltdown on i386.
* Complete mitigation of SpectreV2 at userspace level requires each package to be compiled with retpolines or apply mitigations specific to that software. This is the case for some key components like Abrowser.
* You can see the list of active kernel mitigations at /sys/devices/system/cpu/vulnerabilities/ I'm not sure what program is displayed in the screenshot from the first post, but it seems to be listing applied mitigations.
* You can use online checkers to test web browsers, like https://xlab.tencent.com/special/spectre/spectre_check.html
jxself's AMD chips are immune to the theoretical Meltdown vulnerability.
...but my potato chips are not immune to the practical deep frying menace.
There have been so many threads on the topic over the years, and only now do we learn that Trisquel users have in fact been massively exposed all along to random attacks by unknown bad actors. My trust has evaporated like snow on the devil's toaster.
Computing is overrated, farewell feisty children.
>"Trisquel users have in fact been massively exposed all along to random attacks by unknown bad actors"
Unlikely, since there are no actual known active Spectre/Meltdown exploits. But we have been exposed to the much more effective method of bonking a fellow on the head with a $5 wrench until he gives up his encryption password: https://xkcd.com/538/
Why Trisquel does not mitigate against the $5 wrench method by mailing each of us padded helmets is beyond me.

This is not funny, the OP has now disappeared, and we know why: "There is no mitigation for Meltdown on i386."
That said, it is not possible to confirm the OP's apparent assumption that their machine *is* compromised based on that screenshot. I have no idea how a user could confirm or disconfirm that their machine is or has been compromised before it is too late, but we would do well to remember their last words of wisdom: "I hope I haven't done something stupid in the past using Windows XP e Windows Vista on my old machines where Trisquel is now."
The message OP got in that screenshot was not that their system was actively being attacked by Spectre or Meltdown, but that no mitigations had been applied. Which is true, since there are no mitigations for i386 machines as quidam stated. Also quidam pointed out that some of the Trisquel packages, such as Abrowser, have mitigations applied to them separately. And quidam linked to a website where you can check to see if your browser is vulnerable to Spectre. I've attached the result for my Spectre check with Libremoon.
If OP did do something stupid with Windows on the machine in the past, it wouldn't have had anything to do with Meltdown or Spectre I wouldn't imagine. All I've heard is that it would take a major nation state hacker, someone with unlimited funding and hacking talent and zero ethics, to roll out some true Spectre/Meltdown malware and unleash it in the wild. And if someone put the time and money into doing that, I doubt they would be going after a handful of old i386 boxes. I could be wrong - but it does make sense, think about it - after all these years of Spectre/Meltdown vulnerabilities in the news, we've never heard about a single active exploit. There is one working bit of code that was uploaded a few years ago to a VirusTotal website, but it turns out it was a penetration testing tool for security professionals, and has not so far been turned into any active malware.
> The message OP got in that screenshot was not that their system was actively being attacked by Spectre or Meltdown, but that no mitigations had been applied.
No, that is not what I meant, quite the opposite. OP's screenshot is listing mitigations that *are* applied. My comment about no mitigations existing on i386 *for meltdown specifically* is just a general comment, since it may be useful to bring up within the context of this topic. I didn't mean that it applies to OP in particular.
I see, so the "CPU is affected by ..." language is the description of why the Bug Workaround is applied. So the OP's kernel DOES have Spectre and Meltdown mitigations, and OP IS running a 64-bit system.
The Trisquel kernel does apply Spectre and Meltdown mitigations. When I run spectre-meltdown-checker on my Trisquel 11 system (github.com/speed47/spectre-meltdown-checker) I am protected from all except the two vulnerabilities related to running current microcode. But I do have 12 other mitigations in place.
And when I install and run the hardinfo package I get the same wording as the OP did in the Processor-Bug Workarounds section.
Very good, thank you for clarifying, that was confusing language in the OP's hardinfo window.
This definitively looks like a 32-bit CPU.
The screenshot is likely from hardinfo, which lists hardware and, as I understand it, probably knows about vulnerabilities through a flag set on X86 CPUs by a kernel patch.
Looking in the folder pointed to above, my 64-bit CPU has the PTI mitigation for Meltdown, which was indeed not initially available for 32-bit CPUs. Note that the Ubuntu page info is from 2019, Trisquel 9 Etiona shipped with 4.15 and Mr Larabel was predicting landing of PTI for 32-bit kernels in 4.19 or 5.0 at the earliest, which seems to be confirmed by the Debian security page. Whether upgrading to 4.19 or later would provide that PTI mitigation to the OP's 32-bit PAE capable CPU, I cannot tell.
I don't think it's a 32-bit processor. I looked up Pentium M processors at 2.13 GHz, and they were mobile processors from about 2009. I think that's generally too late for a 32-bit processor.
I posted a link to the Intel spec sheet, you miscreant.
Pentium M processors were released in 2003-2004 (Banias) and 2004-2005 (Dothan): https://en.wikipedia.org/wiki/List_of_Intel_Pentium_M_processors.
Oh you are right, there's one on that list, the Pentium M 770 at 2.13 ghz that could be the one, and it is a 32-bit cpu.
I kind of doubt it though, as the OP's hardinfo screen was showing the same mitigation data as for my 64-bit cpu. So I assume OP is running a 64-bit processor for which the mitigations are available. I found web references to quite a few different model numbers of the 2.13 ghz Pentium M's from later years.
Is your browser by any chance removing embedded links?
I saw it, but how did you know that was the Pentium M that @Piriponzolo was using? I assumed you were guessing.
At some point we need to trust the information provided by the manufacturer.
But the general conclusion remains that the sooner we are able to skip Intel, the better.
The problem with skipping Intel is then you have to figure out a graphics card that works with your system and with libre firmware. Not that easy of a task.
I'd be interested to hear which graphics cards jxself uses. Of course, he's claimed he just works in the tty, so maybe he just uses some simple tty graphics off the motherboard.
I have this: https://www.phoronix.com/review/asus-50-gpu
It works just fine and meets my needs. I don't actually need 4 HDMI ports but it's nice to have.
In terms of terminals there are a number of options. A classic terminal example would be the DEC VT100 but those are quite expensive these days and there are other options too, like https://www.ebay.com/itm/324479617033 (Disclaimer: I do not know the seller and cannot vouch for them; also judging solely from the picture it look like that terminal might have some screen burn-in. Buyer beware. It's only to point out an example anyway.)
The important piece is to have something with an RS-232 serial port which, when combined with an adapter, can plug in to USB on a modern computer. Then: systemctl enable name at domaine --now (If the adapter shows up as ttyUSB0.) Ta da. Problem solved. Proceed to login to Trisquel on your terminal and forget about GPU problems.
EDIT: It looks like the Trisquel forums are trying to be smarter than me and are treating part of the command as an email address. Oh well. I'm sure the information to enable serial TTY login can be found online anyway.
>"I have this: https://www.phoronix.com/review/asus-50-gpu
It works just fine and meets my needs. I don't actually need 4 HDMI ports but it's nice to have."
I remember we talked about that card one when the Phoronix article came out - I'm glad to hear it's working on your KGPE-D16's. That's a very interesting combo - if you maxed out that setup you'd have 32 processor cores, 256 gb ram, and 4 hdmi-connected monitors. That's a serious workstation.
will any geforce gt710 graphics card version
work on free software? If so, will
such a graphics card run on a
librebooted gigabyte ga g41m es2l?
Thanks.
will any geforce gt710 graphics card version work on free software?
https://h-node.org/videocards/view/en/1972/NVIDIA-Corporation-GK208--GeForce-GT-710B---rev-a1-
I bought my RYF-certified D8 from Vikings with such a card, I have the same output like in the h-node page except that I have "Kernel modules: nvidiafb, nouveau". It is a blobless coreboot, not libreboot.
will such a graphics card run on a librebooted gigabyte ga g41m es2l?
No clue, I let someone else answer.
Probably better if you start a new topic related to that gt710 card. Sorry that we got so far off topic in this thread. I'm assuming it's prospero's fault.
Also, I was not being funny when I said that jxself's AMD workstations are immune to Meltdown - all AMD chips are immune to Meltdown. So we should all be considering building workstations like his for our own peace of mind.
I am not sure you are allowed three posts in a row without asking for special authorization. Did you?
> I was not being funny
I cannot deny that you have been rather boring of late. Onzolo Pirip's threads are always a good occasion to post carnival pictures, I am sure he will be back soon. Although he will probably be gone not long after that, since his 32-bit machines are going to run out of security updates at the end of this month. Never too late to worry about Spectre/Meltdown, or so it seems.
Prospero is right: the cpu is a Pentium M770 (Dothan) installed on HP510 notebook.
A clarification: Dear Prospero, I did only post a carnival photo in which a beautiful girl shows her "32 bits", see in this thread https://trisquel.info/en/forum/32-bit-free-freedom-os
My other posts weren't occasions for other jokes, but for asking for solutions to problems or advices.
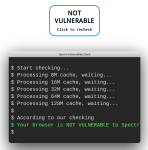
The site https://xlab.tencent.com/special/spectre/spectre_check.html
which I did consult with Abrowser on the 32 bit HP 510 notebook, where Trisquel mini 9.0.2 is installed, gave this result: NOT VULNERABLE. A sigh of relief.
I won't leave this forum because I did install Trisquel mini 10 on an old 64 bit desk pc with cpu Pentium D 950, which has the same situation as Pentium M770 (mobile), as indicated in the initial post of this thread. Also this desk pc is NOT VULNERABLE. I want to hope for the best!
Many thanks to all for the interesting and useful informations.
EDIT: other picture, sorry
Sure, stay with us. Trisquel Mini rocks.
Out of curiosity, what Linux-libre version are you currently using on that HP510?
Also, what is the content of this file: /sys/devices/system/cpu/vulnerabilities/meltdown? On my machine it says "Mitigation: PTI".
Based on reading even this article https://www.techrepublic.com/article/spectre-and-meltdown-explained-a-comprehensive-guide-for-professionals/
I understand that Spectre and Meltdown are wide-ranging hardware flaws that affect the vast majority of devices currently available for sale, devices currently deployed, and legacy devices dating back to the 2000s. I hope I haven't done something stupid in the past using Windows XP e Windows Vista on my old machines where Trisquel is now.
What you need to understand is that Intel is using a different dictionary to ordinary people, and in their dictionary "affected" means "theoretically vulnerable", which is not quite the same thing. Techrepublic is only copy-pasting from Intel, and in turn you are copy-pasting from techrepublic, although you wrote "2000s" instead of "1990s".
The next step is to read Alexandre Oliva's award winning article on the topic, kindly linked to by jxself in the above post. Here is an abstract:
"When we can and do verify that all the software we use can be trusted to do just what we expect, the hardware side channels exploited by Spectre or Meltdown pose no threat, because the software we use serves us.
Any unwanted, deliberate features to obtain information through side channels, and to then transfer it to third parties, would most likely be noticed in individual or community code audits, if not caught as soon as their implementations are contributed to the software project."
When we can and do verify that all the software we use can be trusted to do just what we expect
When I use abrowser, scripts are downloaded not from Trisquel repositories and are executed, and I doubt anyone will ever check what they contain. While I limit the number of sites for which I don't block execution of downloaded scripts, I am still accepting execution of scripts from many sites. Until I am able to reject execution of any script downloaded from anywhere else than Trisquel repositories, having patches for spectre and meltdown seem useful.
It's "useful" to have nonfree software added on to the nonfree software that's already being provided by random strangers on the internet and executed in the browser? Heaping even more nonfree software onto the pile can't be the right answer.
No one in this discussion suggested adding more non-free software, I have no clue what you are talking about.
The sites from which I am having to tolerate scripts are a number of free software projects whose information is only accessible that way (including GNU Jami), the French tax office, the French public health insurrance system, the French property office, the French law official site, some public consummer organization, my bank and I am probably forgetting a few more.
I do not trust that these sites know what they are doing but I have little choice.
"I have no clue what you are talking about."
"Hving patches for spectre and meltdown seem useful."
I recommend reading Alexandre Oliva's blog post then.
Software mitigations have been proposed to make it harder for malicious software to exploit Meltdown and Spectre. Some of the mitigations depend on modified cpu microcode.
It clearly says that there are mitigation that don't depend on modified microcode. If some of these mitigations are free software, I see no valid reason not to use them. I have not searched though.
Please do not lecture people without reading what they actually write, I never suggested using non-free-software to mitigate spectre and meltdown. Such an attitude is likely to alienate people who sincerely support free software.
EDIT: I'd like to add that the lack of verification of software is about all downloaded Javascript, whether it puts headers pretending to be free software or not, as it is never inspected and also that neither Debian maintainers nor Ubuntu nor Trisquel maintainers are in a position to check all free software in the distro.
- Inicie sesión o regístrese para enviar comentarios