Download and verification instructions may need update and links to source of .asc and .md5 files
- Vous devez vous identifier ou créer un compte pour écrire des commentaires
Are the instructions here for verifying a downloaded Trisquel ISO still valid?
https://trisquel.info/en/wiki/download-trisquel
The page contains a reference to Belenos (Trisquel 7) and may not have been updated since that release. Some issues:
* there is an instruction to install gnupg, but in Etiona gnupg is already installed (maybe also in Flidas?)
* the following instruction to add the gpg key produced the following output on my system (a freshly installed Flidas system upgraded to Etiona using the update manager):
gpg: keybox '/home/strypey/.gnupg/pubring.kbx' created
gpg: /home/strypey/.gnupg/trustdb.gpg: trustdb created
gpg: key B138CA450C05112F: public key "Trisquel GNU/Linux <name at domain>" imported
gpg: key B4EFB9F38D8AEBF1: 6 signatures not checked due to missing keys
gpg: key B4EFB9F38D8AEBF1: public key "Trisquel GNU/Linux (Trisquel GNU/Linux signing key) <name at domain>" imported
gpg: no ultimately trusted keys found
gpg: Total number processed: 2
gpg: imported: 2
* The instructions refer to an .asc file but this did not arrive with the ISO (downloaded by torrent). Same with the Md5 file. Where can these be found? I can't see a link to a place I can download these, either on this page, or on the standard download page:
https://trisquel.info/en/download
Using DDG I found this page that has the .asc and .md5 files:
https://cdimage.trisquel.info/trisquel-images/
I have added a link to this page where it says:
> Upon downloading Trisquel you should find an MD5 and GPG link.
Since gnupg is installed by default in Etiona, is there a reason that the Trisquel gpg key is not preinstalled also?
Finally, it would be good if the Download page linked from the main site had a link to those verification instructions but I can't edit the main site.
I am no expert in digital signature. Anyway, as far as I understand, trusting Trisquel's public key, installed by default, would be problematic for those who get Trisquel from a middle-man (handing a USB key for instance) rather than right from Trisquel's server: the distribution may have been tampered (maybe it uses different software repositories full of malware) and you would not know.
Since the end of April 2021 is the scheduled end of support for Ubuntu 16.04 - the base for Flidas - it makes sense to me to update everything on the 'Download Trisquel' wiki page (including the verification instructions) to match the expected behaviour of Etiona. For example, the output of:
> gpg --verify trisquel_9.0_amd64.iso.asc
...was:
> gpg: assuming signed data in 'trisquel_9.0_amd64.iso'
> gpg: Signature made Mon 19 Oct 2020 13:14:55 NZDT
> gpg: using RSA key B138CA450C05112F
> gpg: Good signature from "Trisquel GNU/Linux <name at domain>" [unknown]
> gpg: WARNING: This key is not certified with a trusted signature!
> gpg: There is no indication that the signature belongs to the owner.
> Primary key fingerprint: 6036 4C98 69F9 2450 421F 0C22 B138 CA45 0C05 112F
This doesn't match the expected output on the page, which is:
> gpg: Signature made Mon 03 Nov 2014 04:31:46 AEST using DSA key ID 8D8AEBF1
> gpg: Good signature from "Trisquel GNU/Linux (Trisquel GNU/Linux signing key)"
> gpg: WARNING: This key is not certified with a trusted signature!
> gpg: There is no indication that the signature belongs to the owner.
> Primary key fingerprint: E6C2 7099 CA21 965B 734A EA31 B4EF B9F3 8D8A EBF1
I have no idea what to make of this, but I presume the expected output was that for Belenos ;)
FYI the output of the md5sum instruction matched what the page told me to expect, so that's good.
name at domain writes:
> Since the end of April 2021 is the scheduled end of support for Ubuntu
> 16.04 - the base for Flidas - it makes sense to me to update
> everything on the 'Download Trisquel' wiki page (including the
> verification instructions) to match the expected behaviour of
> Etiona. For example, the output of:
>
>> gpg --verify trisquel_9.0_amd64.iso.asc
>
> ...was:
>
>> gpg: assuming signed data in 'trisquel_9.0_amd64.iso'
>> gpg: Signature made Mon 19 Oct 2020 13:14:55 NZDT
>> gpg: using RSA key B138CA450C05112F
>> gpg: Good signature from "Trisquel GNU/Linux " [unknown]
>> gpg: WARNING: This key is not certified with a trusted signature!
>> gpg: There is no indication that the signature belongs to
> the owner.
>> Primary key fingerprint: 6036 4C98 69F9 2450 421F 0C22 B138 CA45 0C05 112F
>
> This doesn't match the expected output on the page, which is:
What I don't understand is the value of serving the signature from the
same source as the file. If I were malicious and cracked the server such
that I had write access, I would replace the file along with the
signature.
Wouldn't it be better to have the signature distributed via completely
separate server?
--
"Cut your own wood and it will warm you twice"
> What I don't understand is the value of serving the signature from the same source as the file.
I thought the idea was to avoid downloading malicious files from mirrors on which Trisquel devs have no control.
name at domain writes:
>> What I don't understand is the value of serving the signature from
> the same source as the file.
>
> I thought the idea was to avoid downloading malicious files from
> mirrors on which Trisquel devs have no control.
I agree with that. But that doesn't address my question. Please keep in
mind that it may be I who is confused about this, and therefore my
question may be misleading.
To reiterate:
If someone maliciously takes control of the main trisquel server and
replaces both the file and the signature, then an unsuspecting recipient
would download the file, check the signature and see that they match. To
recapitulate this point: if someone has sufficient access to the server
where both the file and the signature are kept, they would replace both
at the same time. In my mind, this limits the value of the signature to
merely telling you that you have successfully downloaded a bit-perfect
copy of the file, and nothing more.
But if the signature is kept somewhere else (perhaps distributed to
several trusted people), then if someone maliciously takes control of
the main trisquel server and replaces the file, then they would have the
additional challenge of breaking into the separate server (or servers)
where the signatures is kept. Then an unsuspecting recipient could still
download the file from the compromised trisquel server, but if they
download the signature from an uncompromised separate server then the
signature would reveal that the file has been tampered with.
I hope that makes more sense.
--
"Cut your own wood and it will warm you twice"
> Please keep in mind that it may be I who is confused about this, and therefore my question may be misleading.
Honestly, if one of us is confused, then it must be me. Computing is very demanding for my troubled troubadour mind.
I naively thought that if someone was to usurp admin privileges on the trisquel.info server, it would not be long before the situation is taken care of and the genuine files returned. However, if someone was to modify the ISO files on trisquel-rocks.cool-download.me, then it might never come to the attention of the Trisquel devs but the verification process will still show that the file has been tampered with.
Maybe my mind has been tampered with, though, and I am only following unconscious biases inserted by random hackers. Where can I find the md5 hash file for my genuine mind?
What is the md5 hash file for your genuine mind?
I also might want one if there is such a thing.
Of course I want the md5 hash file for my genuine mind, not for your genuine mind.
Because the md5 hash for your genuine mind would not match my genuine mind exactly.
As far as I understand, a plain signature is only useful to check that the file is not corrupted in the transfer, besides that it does not help for anything.
What helps is if the signature is encrypted and you can decrypt it with a public key that you have some confidence was generated by Trisquel's maintainers. See https://www.gnupg.org/gph/en/manual.html#AEN216 for some explanations.
name at domain writes:
> As far as I understand, a plain signature is only useful to check that
> the file is not corrupted in the transfer, besides that it does not
> help for anything.
>
> What helps is if the signature is encrypted and you can decrypt it
> with a public key that you have some confidence is used by Trisquel's
> maintainers. See https://www.gnupg.org/gph/en/manual.html#AEN216 for
> some explanations.
That helps explain it; thank you.
--
"Cut your own wood and it will warm you twice"
My apologies: each time you wrote "signature", my compromised mind interpreted "md5". Sorry for the confusion. And thank you Avron for clarifying.
Checking for the integrity of the file after download is not a bad idea. I will do it now, I only did md5sum in the past.
The download page has links to verification files once the download is initiated.
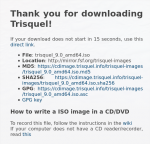
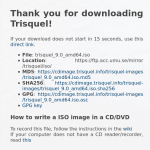
True, but I could find no way to get back to that page once I closed it. Can you provide the URL for that page?
https://trisquel.info/en/download
Select the iso you downloaded, click on the "Download ISO" button and cancel the download in the pop-up window. Then download the verification file of your choice.
EDIT: In fact you do not even need to close the pop-up window, the file path will update after you click on the link pointing to the verification file.
lanun:
> Then download the verification file of your choice.
I cannot see any way to download verification files anywhere on this page.
I can. But I need to select "Download ISO" first, which makes sense since each ISO has different verification files.
lanun:
> I can. But I need to select "Download ISO" first, which makes sense since each ISO has different verification files.
Right, but if I've already downloaded the ISO and I didn't get the verification files on the first round, putting text like 'verification files for all versions' on the download page, linked to the second URL you gave, would be quite helpful. Putting the verification files in the torrent would be even better.
The dotted list shown in loldier's screenshots would indeed nicely fit in the "Select a mirror" frame on the initial download page, before the "Download" buttons and hence before the user's focus shifts away from the page.
You might want to send a suggestion to: https://trisquel.info/en/contact.
Alternatively: http://cdimage.trisquel.info/trisquel-images
FYI I just downloaded the 32-bit version of Trisquel 9 using the torrent. The links for the verification files looked like this:
> File: trisquel_9.0_i686.iso.torrent
> Location: https://cdimage.trisquel.info/trisquel-images
> MD5: https://cdimage.trisquel.info/trisquel-images/trisquel_9.0_i686.iso.torrent.md5
> SHA256: https://cdimage.trisquel.info/trisquel-images/trisquel_9.0_i686.iso.torrent.sha256
> GPG: https://cdimage.trisquel.info/trisquel-images/trisquel_9.0_i686.iso.torrent.asc
> GPG key
Clicking on most of these links throws an error:
> Not Found
> The requested URL was not found on this server.
I'm guessing because of the ".torrent" in the file names? When I tried again with "Download ISO" instead of "Download Torrent", the links are correct. The same thing happens when downloading the 64-bit version using the torrent, so the problem probably occurs with all torrent downloads.
Indeed. Only the torrent file itself should have the 'torrent' extension in its name.
The MD5, SHA256 and GPG files are the same, since they refer to the same ISO.
I've tried to fix this long-standing issue (again). I think everything should be properly this time.
Thanks for the report!
- Vous devez vous identifier ou créer un compte pour écrire des commentaires

