Submitted by GNUtoo on Tue, 11/10/2009 - 14:51
Revision of Full Disk Encryption Install from Tue, 02/07/2012 - 08:10
The revisions let you track differences between multiple versions of a post.
This manual describes how to install Trisquel onto an encrypted hard drive:
- swap will be encrypted.
- root (/) will be encrypted.
- boot (/boot) cannot be encrypted but could be on an USB key or non-rewritable CD-ROM (not covered here).
New Instructions
- Boot into the liveCD environment and from the installation menu select "Install Trisquel in text mode"
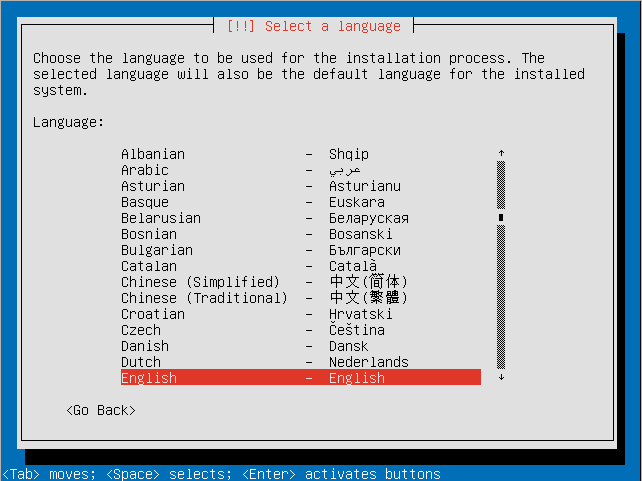
- Select a language.
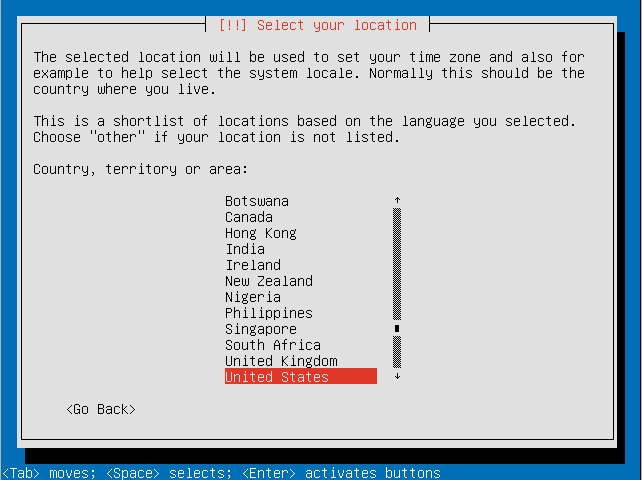
- Select your location.
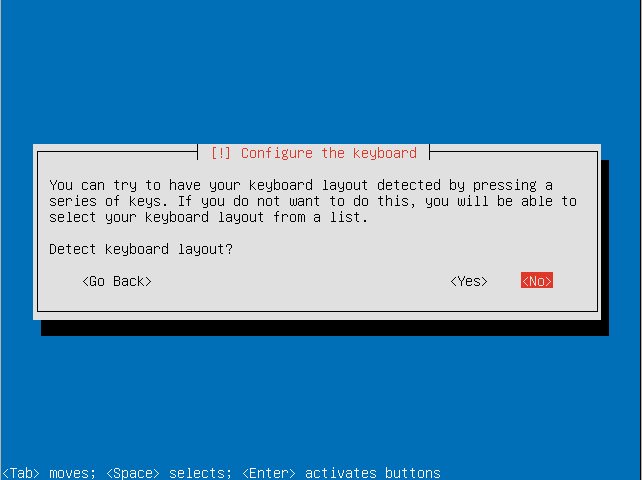
- Decide if you want the installer to detect your keyboard.
- Choose the country of origin for your keyboard.
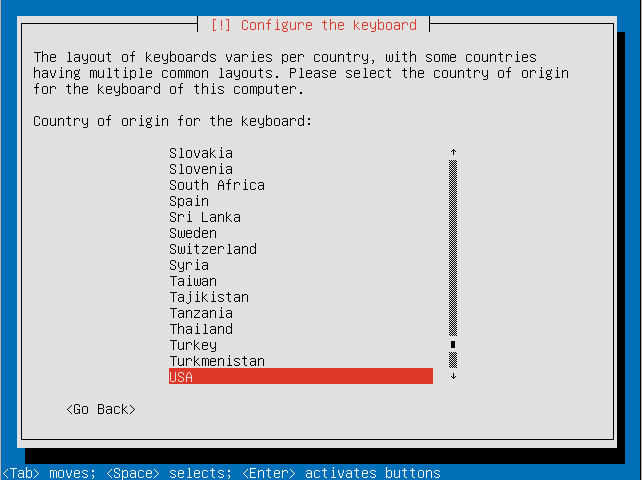
- Select your keyboard layout.
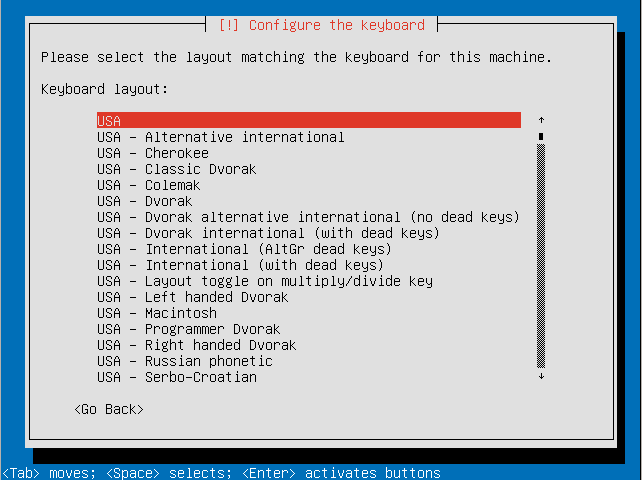
- Choose a hostname for your system.
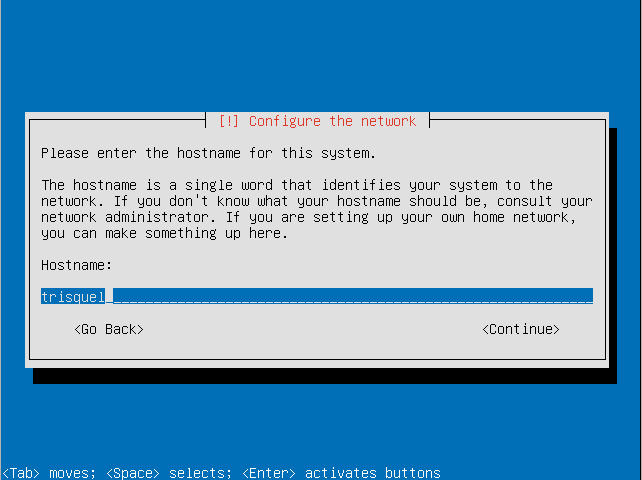
- Choose a country for your preferred mirror.
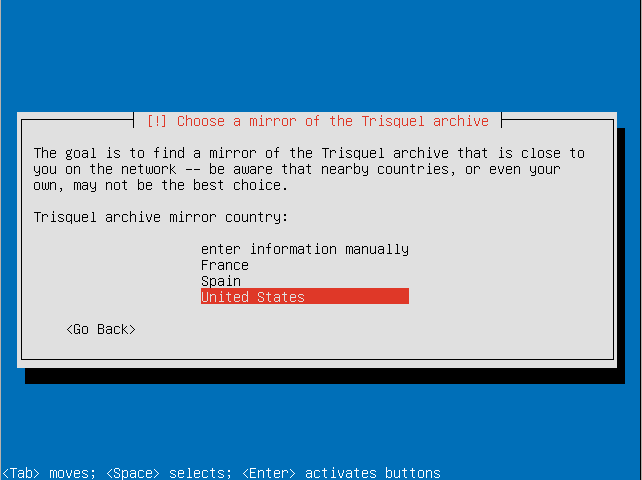
- Select a Trisquel mirror.
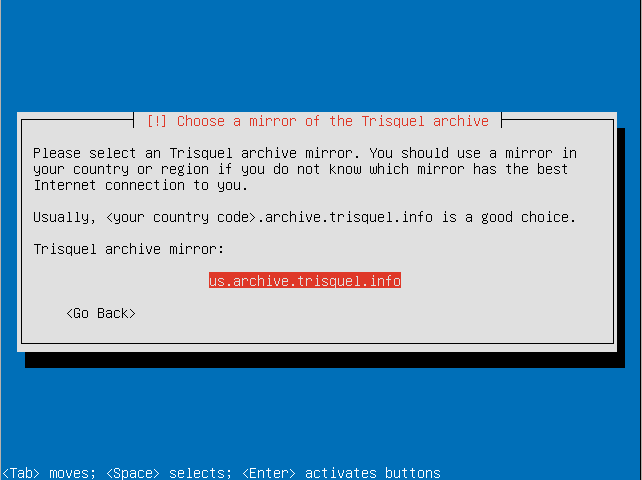
- If you require a proxy to access the Internet enter the information here.
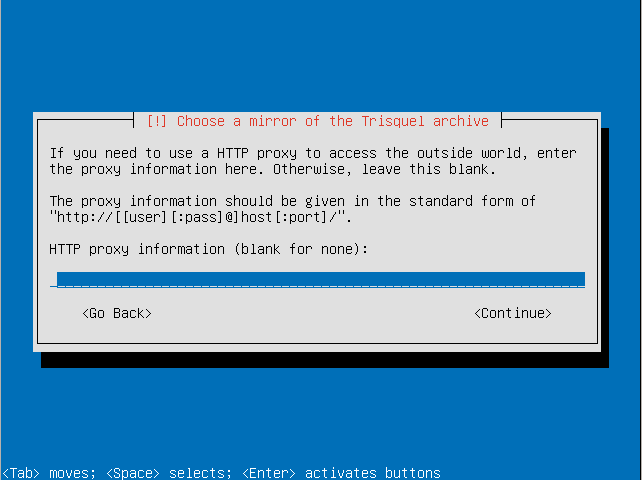
- Make sure the timezone the installer detected is correct.
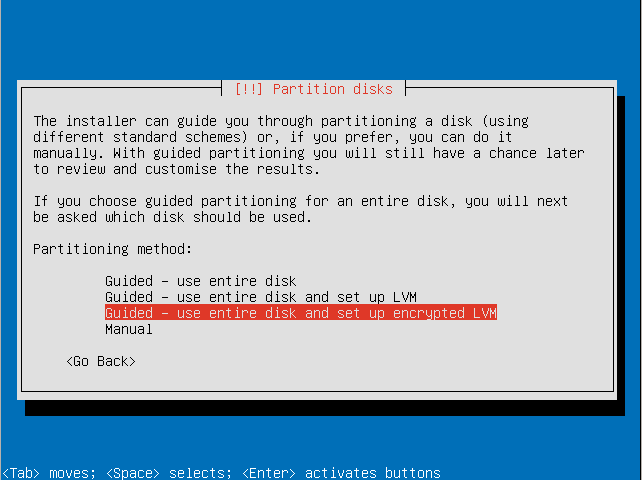
- Choose the "Guided - use entire disk and set up encrypted LVM" option.
- Select the disk to install Trisquel on.
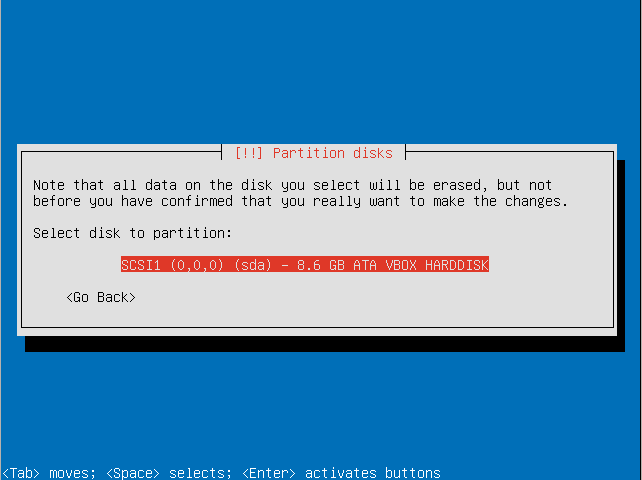
- Confirm that you are willing to write the changes to disk and configure the LVM.
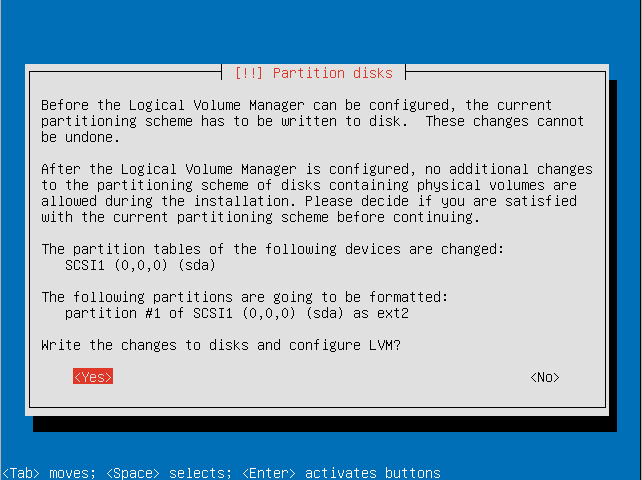
- Enter an encryption passphrase.
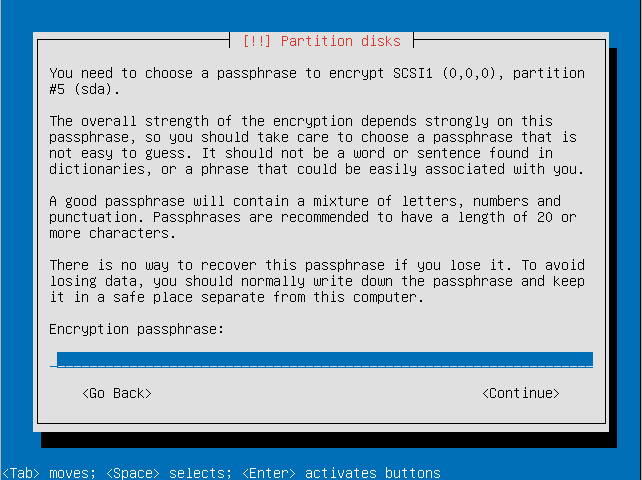
- Resubmit the passphrase to verify it.
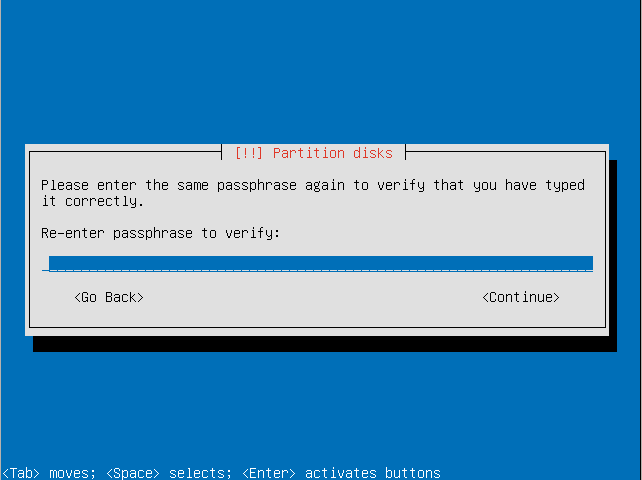
- Choose the amount of the volume group to use for guided partitioning.
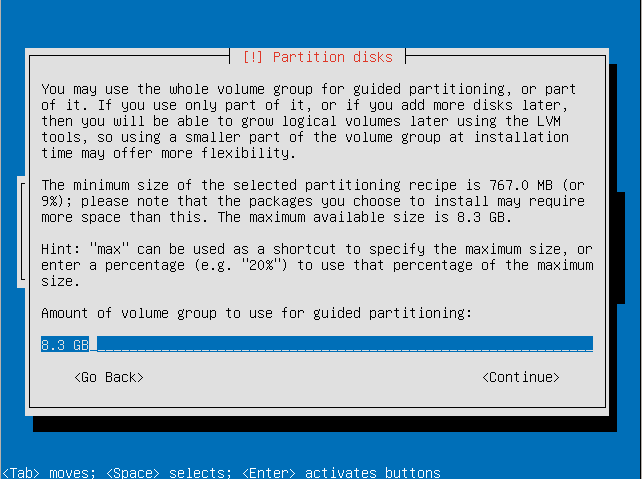
- Confirm that you want to write changes to the disk.
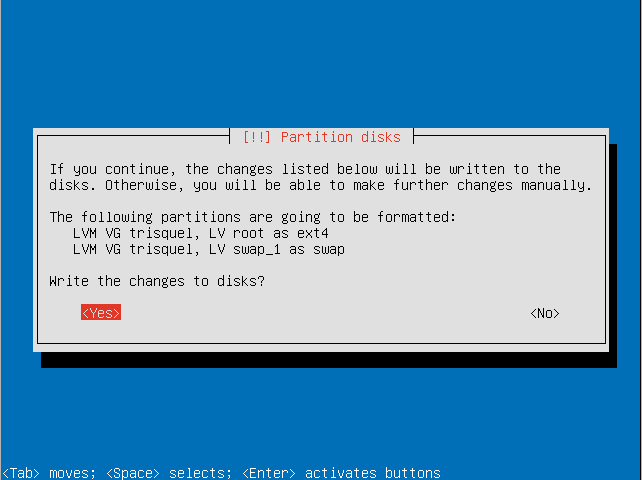
- Select a kernel to install.
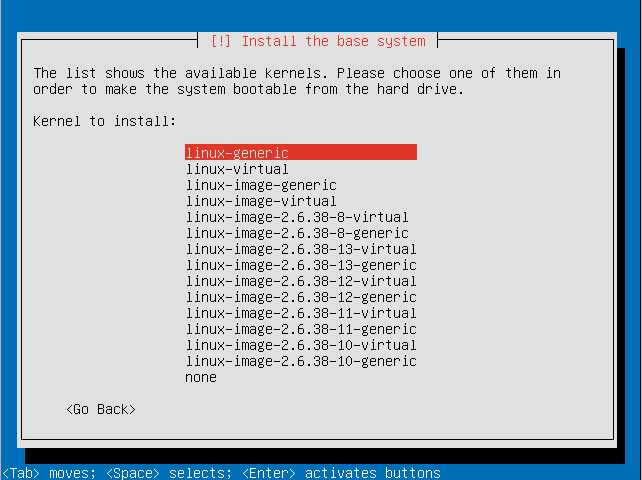
- Enter the full name for the use account that will be created.
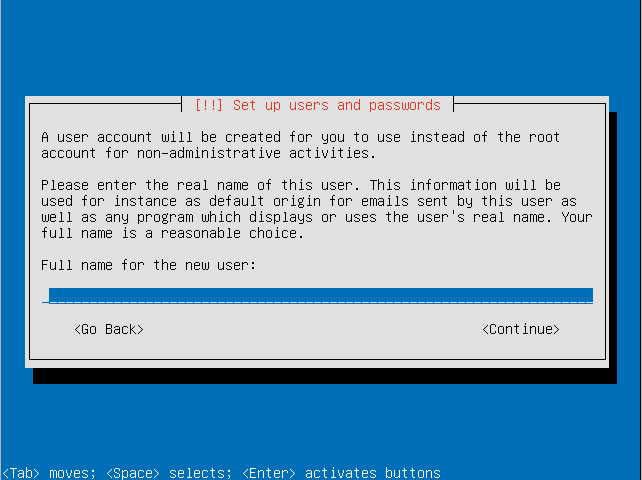
- Choose a username for the user account.
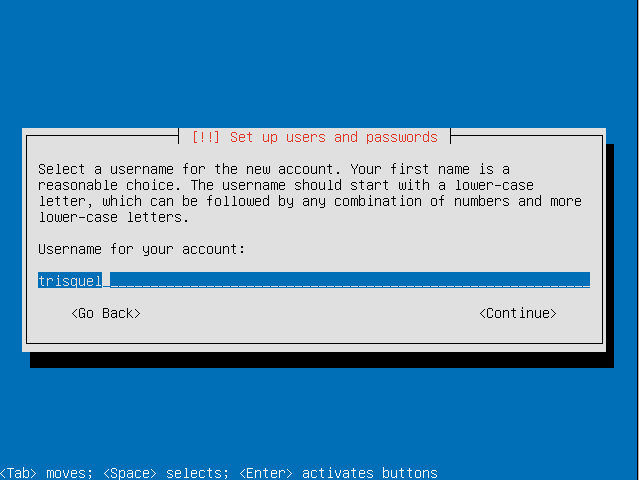
- Choose a password for the user.
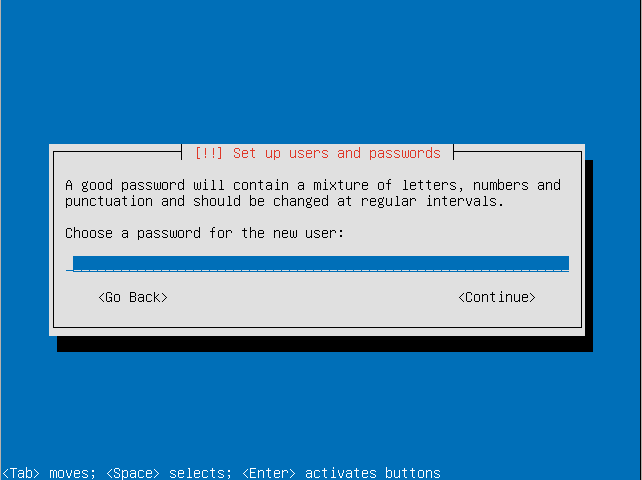
- Re-enter the password to verify it.
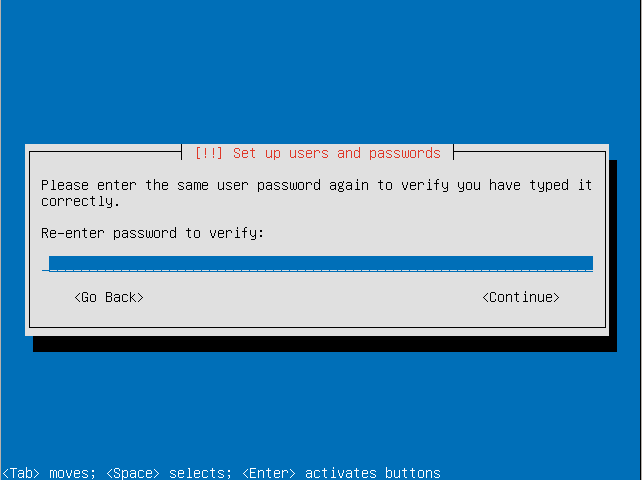
- Choose if you want to also encrypt your home directory. This can be useful for a computer with multiple users even if the LVM itself is encrypted.
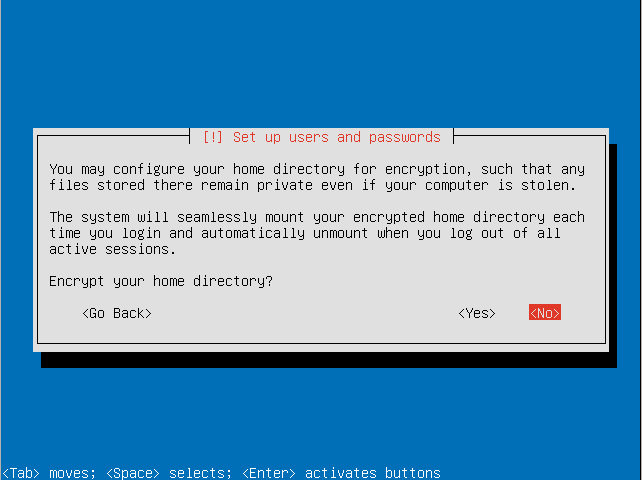
- Decide how you want to manage upgrades on your system.
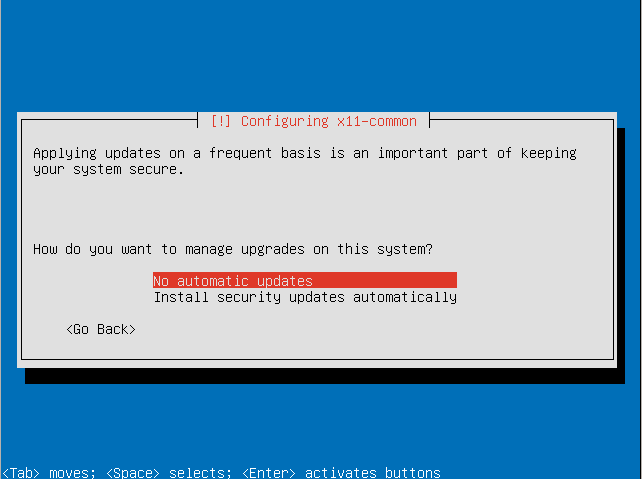
- Choose the software sets you want to install. For this tutorial we will be installing the default Trisquel desktop environment.
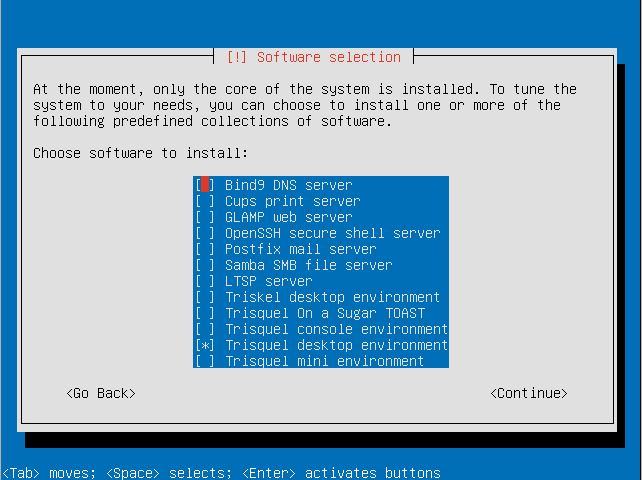
- Select continue to continue software configuration.
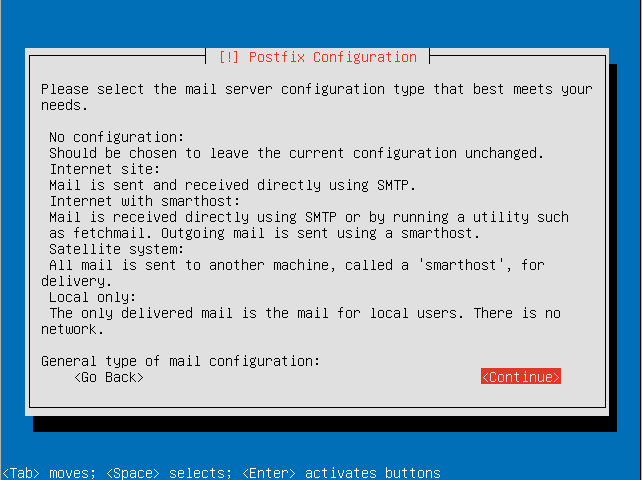
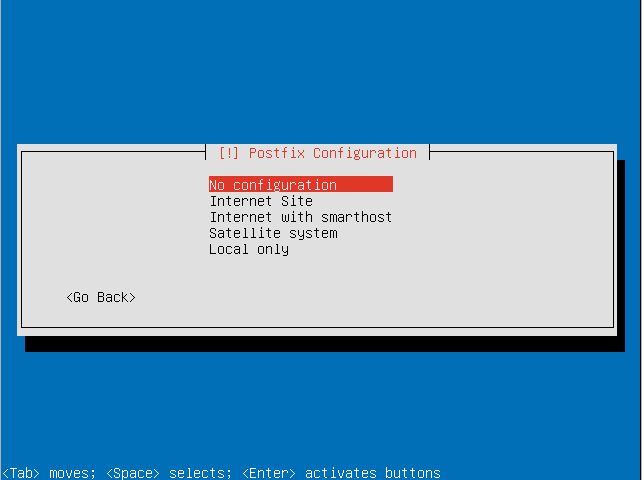
- Configure postfix (if you wish to have an email server).
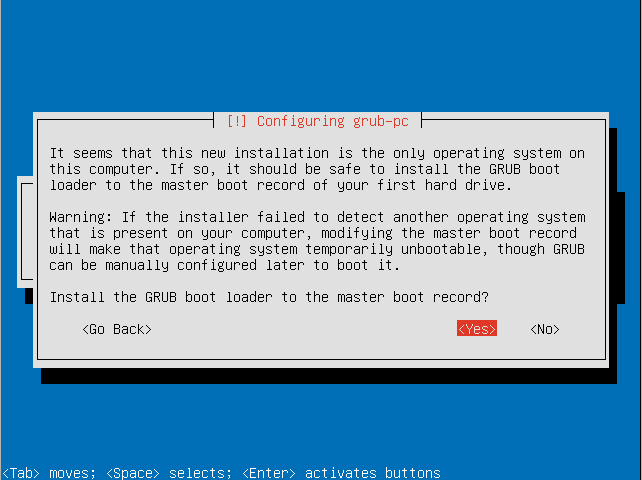
- Decide if you want to install the GRUB boot loader to the master boot record.
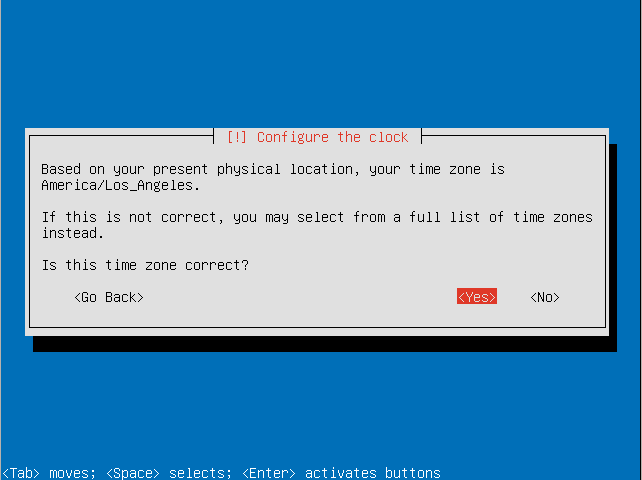
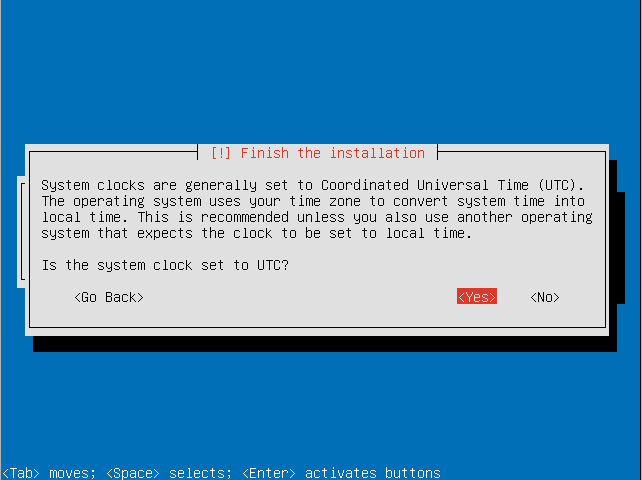
- Select if your system clock is set to UTC.
Instructions
- Boot the CD, DVD, or USB thumb drive into the live environment.
- Connect to the network using NetworkManager (located on the far-right side of the Panel).
- Open the terminal and become root:
sudo su
- Install cryptsetup and gparted:
apt-get update apt-get install gparted apt-get install cryptsetup
- Launch gparted and partition your hard disk like you would do normally (so create filesystem on the partition etc...) creating unencrypted valid partitions.
- Use Wikipedia to find a good block cypher. One example is aes,xts,essiv:256.
- Load the modules of the chosen encryption:
modprobe xts modprobe aes_i586 modprobe sha256Note that aes_i586 is an optimized version of aes for i586 or later X86 CPU. For a 64 bit architecture (amd64), you have to load the aes_x86_64 module.
- Format the partition you have chosen for root(/) with cryptsetup:
cryptsetup -y --cipher aes-xts-essiv:sha256 --key-size 512 luksFormat /dev/PARTITION
- Replace /dev/PARTITION by your partition. It will overwrite all the data in the partition.
- Open the partition (replace /dev/PARTITION as needed):
cryptsetup luksOpen /dev/PARTITION crypto_root
- Format the partition using the filesystem you want (preferably ext4, or XFS if you don't mind that partitions cannot be shrunk in XFS). For an ext4 filesystem, run:
mkfs.ext4 /dev/mapper/crypto_root
- Launch the Trisquel installer and proceed to step 4, hard disk partitioning.
- Select manual partitioning, then select your root (/) partition to be /dev/mapper/crypto_root.
- Select your swap partition
- Select your unencrypted /boot partition
- Be careful not to recreate the partition table.
- Proceed with installation. When it finishes, select to continue trying Trisquel. Do not reboot.
- Mount your root partition and chroot into it:
mkdir /mnt/root mount /dev/mapper/crypto_root /mnt/root mount /dev/ /mnt/root/dev -o bind chroot /mnt/root mount /proc chroot /mnt/root mount /sys chroot /mnt/root
- Create the /etc/crypttab replacing /dev/PARTITION as needed:
echo "root /dev/disk/by-uuid/$(blkid -o value -s UUID /dev/PARTITION) none luks" >> /etc/crypttab
- Add the cypher modules you have chosen before to /etc/modules so they load at boot and get included in the initd:
echo xts >> /etc/initramfs-tools/modules echo aes_i586 >> /etc/initramfs-tools/modules echo aes_x86_64 >> /etc/initramfs-tools/modules # for amd64 arch echo sha256 >> /etc/initramfs-tools/modules
- Install cryptsetup:
apt-get update apt-get install cryptsetup
- Rebuild the initrd:
mount /boot update-initramfs -u
- Exit the chroot and unmount everything:
exit umount /mnt/root/boot umount /mnt/root/proc umount /mnt/root/dev umount /mnt/root/sys
- Finally, reboot Trisquel. You will be asked for your hard disk encryption password.
Revisions
10/18/2011 - 17:49
anonymous

