Revision of Freenode with Tor from Thu, 08/02/2012 - 08:55
The revisions let you track differences between multiple versions of a post.
The goal of this manual is to allow you to connect to the Freenode IRC server using Tor. This could be because a user wishes to remain anonymous or is in an area where Freenode is blocked. This is an intermediate level manual and assumes you are comfortable with using the terminal (or at minimum copy and pasting commands) and understand the basics of Tor.
Warning: Connecting to Freenode using these directions eliminates the primary benefit of Tor. You will not be anonymous. What you will be able to do is bypass censorship. Tor users will only appear anonymous to other users and identification is still possible. If anonymity is required users should consider other IRC networks.
Required Software
Optional Software
- xchat-otr: OTR encryption plugin for xchat
Prerequisites
- A registered and verified freenode nick. This is REQUIRED!
Security Precautions/Concerns
- A prerequisite is a registered and verified freenode nick. This requires you to connect firstly to freenode without tor and using an email address. This may compromise your identity if not done properly. Users requiring stronger anonymity should in this case:
- Register their nick in a location as far away as possible from their normal location. Register in a public location (e.g. coffee shop, library, university). If possible register in an area with lots of tor users (e.g. a large city) because if you are the only tor user in your area it may be easier to track you down.
- Connect to FreeNode using their SSL service to prevent snooping.
- Change your password once you return to your normal location in case it was compromised in public.
- Do not use your regular email address when registering. Use tor and your browser to create a dummy email address for email verification.
- The SASL plug-in XChat uses saves your password in clear-text in your XChat configuration folder.
- Encrypt your hard drive or home directory to prevent someone from accessing your password.
- Do not re-use the password for other programs.
- Change your password often or if you feel your identity has been compromised, abandon that identity.
Sample Account
For the example used here we will use a sample account with the following information:- Username: TrisquelwithTor
- Password: GNULinuxLibre
Full Instructions
- Install required and optional software:
$ sudo apt-get -y install libcrypt-blowfish-perl libcrypt-dh-perl libcrypt-openssl-bignum-perl tor xchat xchat-otr
- Download SASL authentication plug-in (GPL):
$ cd ~/.xchat2 $ wget http://lwsitu.com/xchat/cap_sasl_xchat.pl
- (Recommended): Change connection timeout on SASL plugin:
$ sed 's/my $AUTHENTICATION_TIMEOUT = 5;/my $AUTHENTICATION_TIMEOUT = 45;/g' ~/.xchat2/cap_sasl_xchat.pl -i
- Open XChat and the Network list screen should display. Fill in the Nick name, User name, and Real name fields. Then select the FreeNode network and click Edit to configure the network settings.
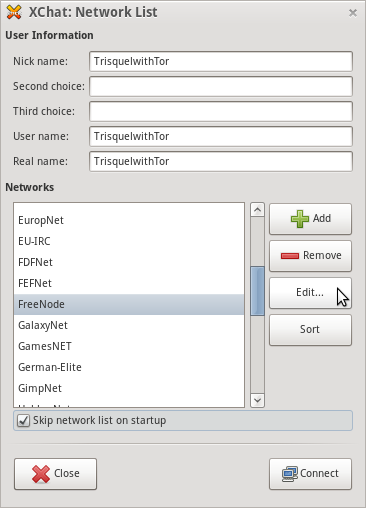
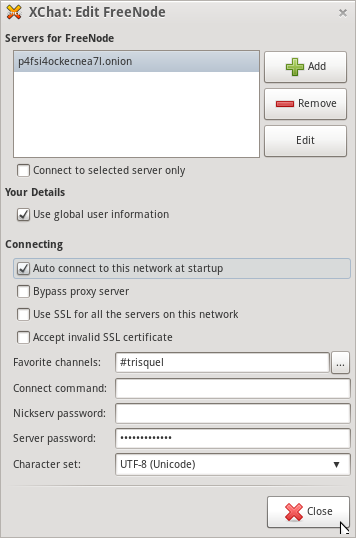
- Edit the server address to the IRC hidden service p4fsi4ockecnea7l.onion. Input the password for your registered freenode nick in the Server password field. Lastly, select select Character set "UTF-8 (Unicode). You may also select additional options such as auto-joining channels and automatic connection.
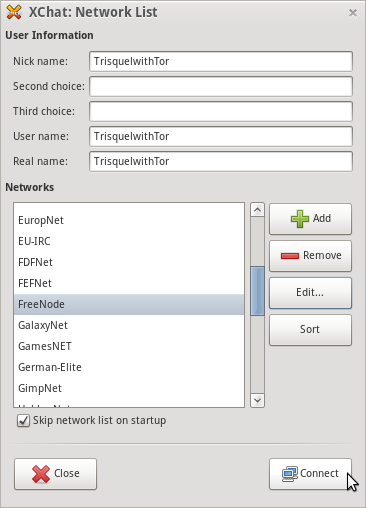
- At the Network list select FreeNode and click "Connect"
- In the input field enter the SASL information required:
/SASL set FreeNode TrisquelwithTor GNULinuxLibre DH-BLOWFISH
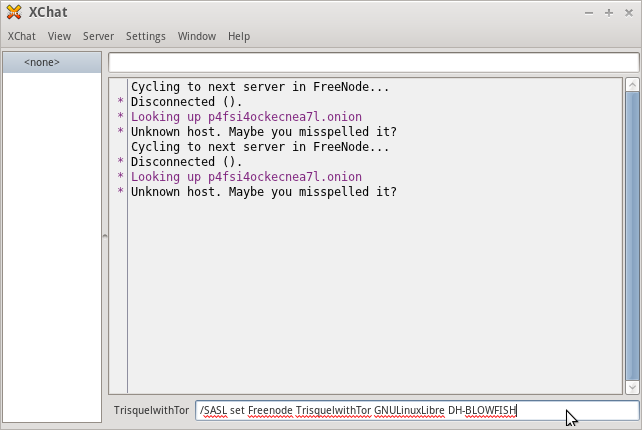
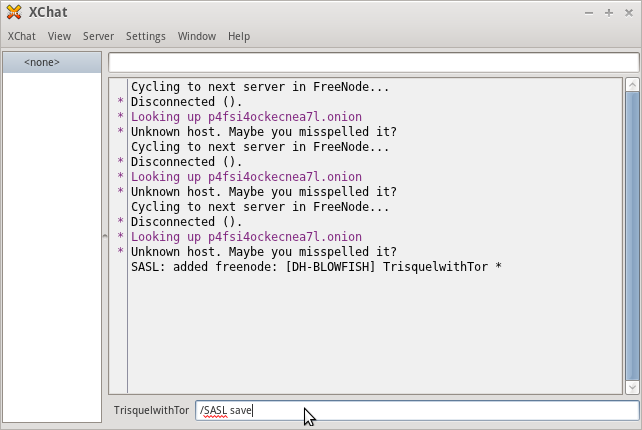
- Save the SASL information. This retains your SASL information so you do not have to enter it every time. (Optional)
/SASL save
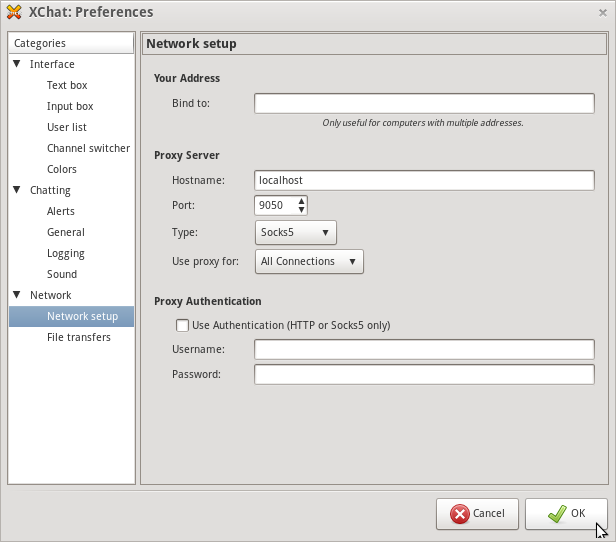
- In the XChat preferences set the Proxy Server information to use tor with the following information
Hostname: localhost Port: 9050 Type: Socks5 Use Proxy For: All Connections
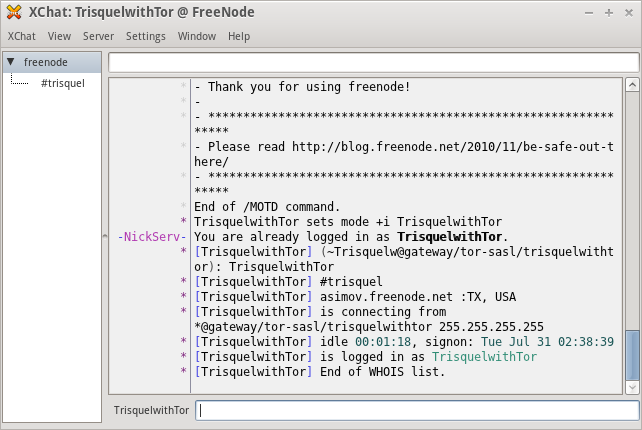
- At this point XChat may attempt to connect and experience a OpenSSL error. Restart XChat and connect to FreeNode and XChat will connect using Tor. You can verify that you are using Tor by running the command "whois" on your nick.