No automatic updates
- Login o registrati per inviare commenti
I am running Nabia 10.0.1 with Mate 1.24.0. Since my upgrade from 9.0, the system has not been updating automatically.
I can update manually via terminal without any problems.
My main menu has both Software & Updates and Software Updater, both of which are set to
check/display updates daily from the main server. But no updates are ever shown.
Any suggestions would be greatly appreciated. I am trying to avoid doing a reinstall.
Thanks!
Some additional info. I manually upgraded today and then ran unattended-upgrades in debug mode. It complains that it could not figure out the development release.
Log unattended-upgrades:
2022-05-18 16:03:29,085 WARNING Could not figure out development release: Distribution data outdated. Please check for an update for distro-info-data. See /usr/share/doc/distro-info-data/README.Debian for details.
2022-05-18 16:03:29,086 INFO Starting unattended upgrades script
2022-05-18 16:03:29,088 INFO Allowed origins are: o=Trisquel,a=nabia, o=Trisquel,a=nabia-security, o=TrisquelESMApps,a=nabia-apps-security, o=TrisquelESM,a=nabia-infra-security
2022-05-18 16:03:29,088 INFO Initial blacklist:
2022-05-18 16:03:29,089 INFO Initial whitelist (not strict):
2022-05-18 16:03:29,509 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:03:29,510 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:03:29,510 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:03:29,510 DEBUG Applying pinning: PkgFilePin(id=6, priority=-32768)
2022-05-18 16:03:29,510 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:03:29,510 DEBUG Applying pinning: PkgFilePin(id=5, priority=-32768)
2022-05-18 16:03:29,510 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:03:29,510 DEBUG Applying pinning: PkgFilePin(id=4, priority=-32768)
2022-05-18 16:03:29,511 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:03:29,526 DEBUG Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
2022-05-18 16:03:29,526 DEBUG Using (^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$|^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$) regexp to find running kernel packages
2022-05-18 16:03:30,756 DEBUG pkgs that look like they should be upgraded:
2022-05-18 16:03:30,790 DEBUG fetch.run() result: 0
2022-05-18 16:03:30,833 DEBUG Packages blacklist due to conffile prompts: []
2022-05-18 16:03:30,834 INFO No packages found that can be upgraded unattended and no pending auto-removals
2022-05-18 16:03:31,323 DEBUG Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2022-05-18 16:03:29
2022-05-18 16:10:15,394 WARNING Could not figure out development release: Distribution data outdated. Please check for an update for distro-info-data. See /usr/share/doc/distro-info-data/README.Debian for details.
2022-05-18 16:10:15,395 INFO Starting unattended upgrades script
2022-05-18 16:10:15,396 ERROR Lock could not be acquired (another package manager running?)
2022-05-18 16:10:15,397 DEBUG Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2022-05-18 16:10:15
2022-05-18 16:10:49,310 WARNING Could not figure out development release: Distribution data outdated. Please check for an update for distro-info-data. See /usr/share/doc/distro-info-data/README.Debian for details.
2022-05-18 16:10:49,311 INFO Starting unattended upgrades script
2022-05-18 16:10:49,312 INFO Allowed origins are: o=Trisquel,a=nabia, o=Trisquel,a=nabia-security, o=TrisquelESMApps,a=nabia-apps-security, o=TrisquelESM,a=nabia-infra-security
2022-05-18 16:10:49,313 INFO Initial blacklist:
2022-05-18 16:10:49,313 INFO Initial whitelist (not strict):
2022-05-18 16:10:49,763 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:10:49,763 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:10:49,763 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:10:49,764 DEBUG Applying pinning: PkgFilePin(id=6, priority=-32768)
2022-05-18 16:10:49,764 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:10:49,764 DEBUG Applying pinning: PkgFilePin(id=5, priority=-32768)
2022-05-18 16:10:49,764 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:10:49,764 DEBUG Applying pinning: PkgFilePin(id=4, priority=-32768)
2022-05-18 16:10:49,764 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:10:49,781 DEBUG Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
2022-05-18 16:10:49,783 DEBUG Using (^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$|^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$) regexp to find running kernel packages
2022-05-18 16:10:50,999 DEBUG pkgs that look like they should be upgraded:
2022-05-18 16:10:51,030 DEBUG fetch.run() result: 0
2022-05-18 16:10:51,074 DEBUG Packages blacklist due to conffile prompts: []
2022-05-18 16:10:51,074 INFO No packages found that can be upgraded unattended and no pending auto-removals
2022-05-18 16:10:51,575 DEBUG Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2022-05-18 16:10:49
2022-05-18 16:11:13,640 WARNING Could not figure out development release: Distribution data outdated. Please check for an update for distro-info-data. See /usr/share/doc/distro-info-data/README.Debian for details.
2022-05-18 16:11:13,641 INFO Starting unattended upgrades script
2022-05-18 16:11:13,642 INFO Allowed origins are: o=Trisquel,a=nabia, o=Trisquel,a=nabia-security, o=TrisquelESMApps,a=nabia-apps-security, o=TrisquelESM,a=nabia-infra-security
2022-05-18 16:11:13,642 INFO Initial blacklist:
2022-05-18 16:11:13,643 INFO Initial whitelist (not strict):
2022-05-18 16:11:14,084 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:11:14,084 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:11:14,084 DEBUG Marking not allowed with -32768 pin
2022-05-18 16:11:14,085 DEBUG Applying pinning: PkgFilePin(id=6, priority=-32768)
2022-05-18 16:11:14,085 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:11:14,085 DEBUG Applying pinning: PkgFilePin(id=5, priority=-32768)
2022-05-18 16:11:14,085 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:11:14,085 DEBUG Applying pinning: PkgFilePin(id=4, priority=-32768)
2022-05-18 16:11:14,085 DEBUG Applying pin -32768 to package_file:
2022-05-18 16:11:14,101 DEBUG Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
2022-05-18 16:11:14,102 DEBUG Using (^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$|^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$) regexp to find running kernel packages
2022-05-18 16:11:15,307 DEBUG pkgs that look like they should be upgraded:
2022-05-18 16:11:15,339 DEBUG fetch.run() result: 0
2022-05-18 16:11:15,382 DEBUG Packages blacklist due to conffile prompts: []
2022-05-18 16:11:15,383 INFO No packages found that can be upgraded unattended and no pending auto-removals
2022-05-18 16:11:15,884 DEBUG Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2022-05-18 16:11:13
*********
(Note- I used synaptic to check distro-info-data and the package is up to date.)
Contents of distro-info-data file:
distro-info-data (0.43ubuntu1.10+10.0trisquel2) nabia; urgency=medium
* Adding trisquel distro info.
-- Trisquel GNU/Linux developers <name at domain> Wed, 27 Apr 2022 06:36:07 +0000
distro-info-data (0.43ubuntu1.10) focal; urgency=medium
* Add Ubuntu 22.10, Kinetic Kudu (LP: #1970227)
-- Paride Legovini <name at domain> Tue, 26 Apr 2022 19:26:00 +0200
distro-info-data (0.43ubuntu1.9) focal; urgency=medium
* Add Ubuntu 22.04, Jammy Jellyfish (LP: #1947368).
* Update ubuntu.csv contents to what we had in hirsute+.
-- Łukasz 'sil2100' Zemczak <name at domain> Fri, 15 Oct 2021 14:48:46 +0200
distro-info-data (0.43ubuntu1.8) focal-security; urgency=medium
* Update ubuntu.csv for trusty and xenial ESM extended dates
(LP: #1946137).
-- Leonidas Da Silva Barbosa <name at domain> Wed, 06 Oct 2021 09:28:43 -0300
distro-info-data (0.43ubuntu1.6) focal; urgency=medium
* Move Ubuntu EoLs off weekend days. (LP: #1939457)
-- Brian Murray <name at domain> Tue, 10 Aug 2021 15:12:42 -0700
distro-info-data (0.43ubuntu1.5) focal; urgency=medium
* Add Ubuntu 21.10, Impish Indri (LP: #1925484)
-- Iain Lane <name at domain> Thu, 22 Apr 2021 13:15:23 +0100
distro-info-data (0.43ubuntu1.4) focal; urgency=medium
* Add Ubuntu 21.04, Hirsute Hippo (LP: #1901361).
-- Brian Murray <name at domain> Wed, 28 Oct 2020 12:18:28 -0700
distro-info-data (0.43ubuntu1.1) focal; urgency=medium
* Copy from Debian unstable (0.44):
- Add Ubuntu 20.10, Groovy Gorilla. (LP: #1874843)
- Add a guessed EOL date for Debian Stretch.
-- Stefano Rivera <name at domain> Fri, 24 Apr 2020 08:44:41 -0700
distro-info-data (0.43ubuntu1) focal; urgency=medium
* Merge from Debian unstable. Remaining changes:
- Add in eol-server and eol-esm dates for all Ubuntu LTS releases.
-- dann frazier <name at domain> Mon, 27 Jan 2020 14:28:18 -0700
distro-info-data (0.43) unstable; urgency=medium
* Add Ubuntu 20.04 LTS, Focal Fossa.
* Bump Standards-Version to 4.4.1, no changes needed.
-- Stefano Rivera <name at domain> Thu, 17 Oct 2019 13:10:30 -0700
# For older changelog entries, run 'apt-get changelog distro-info-data'
Thanks for reporting, some issues has been fixed, please install the latest distro-info-data and unattended-upgrades when available, and try again.
Ark74- Thank you.
I ran the update and upgraded the two packages. Then I ran unattended-upgrade in debug mode. (Output below.)
The system is no longer complaining about the development release. But since my system is already up to date, I do not yet know if the updater is actually working. Will report back.
Thanks again.
$ sudo unattended-upgrade -d
Running on the development release
Starting unattended upgrades script
Allowed origins are: o=Trisquel,a=nabia, o=Trisquel,a=nabia-security
Initial blacklist:
Initial whitelist (not strict):
Marking not allowed with -32768 pin
Marking not allowed with -32768 pin
Marking not allowed with -32768 pin
Applying pinning: PkgFilePin(id=6, priority=-32768)
Applying pin -32768 to package_file:
Applying pinning: PkgFilePin(id=5, priority=-32768)
Applying pin -32768 to package_file:
Applying pinning: PkgFilePin(id=4, priority=-32768)
Applying pin -32768 to package_file:
Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
Using (^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$|^linux-.*-5\.4\.0\-110\-generic$|^linux-.*-5\.4\.0\-110$|^kfreebsd-.*-5\.4\.0\-110\-generic$|^kfreebsd-.*-5\.4\.0\-110$|^gnumach-.*-5\.4\.0\-110\-generic$|^gnumach-.*-5\.4\.0\-110$|^.*-modules-5\.4\.0\-110\-generic$|^.*-modules-5\.4\.0\-110$|^.*-kernel-5\.4\.0\-110\-generic$|^.*-kernel-5\.4\.0\-110$) regexp to find running kernel packages
pkgs that look like they should be upgraded:
Fetched 0 B in 0s (0 B/s)
fetch.run() result: 0
Packages blacklist due to conffile prompts: []
No packages found that can be upgraded unattended and no pending auto-removals
Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2022-05-19 09:06:13
My automatic updates are apparently still not working. Packages are not updating and I am receiving no update notifications.
I ran the following this morning:
ege@ege-ThinkPad-X200:~$ apt list --upgradable
Listing... Done
abrowser-locale-en/nabia-updates 100.0.2+build1-0ubuntu0.20.04.1+10.0trisquel87 amd64 [upgradable from: 100.0+build2-0ubuntu0.20.04.1+10.0trisquel87]
abrowser-locale-ga/nabia-updates 100.0.2+build1-0ubuntu0.20.04.1+10.0trisquel87 amd64 [upgradable from: 100.0+build2-0ubuntu0.20.04.1+10.0trisquel87]
abrowser/nabia-updates 100.0.2+build1-0ubuntu0.20.04.1+10.0trisquel87 amd64 [upgradable from: 100.0+build2-0ubuntu0.20.04.1+10.0trisquel87]
icedove/nabia-updates 1:91.9.1+build1-0ubuntu0.20.04.1+10.0trisquel14 amd64 [upgradable from: 1:91.8.1+build1-0ubuntu0.20.04.1+10.0trisquel14]
Additional info-- Var log from yesterday and this morning.
The upgrade script is running but did not upgrade several packages including Icedove and abrowser. Also I received no notification of the available upgrades.
Log:
2022-05-21 06:44:44,337 INFO No packages found that can be upgraded unattended and no pending auto-removals
2022-05-22 06:55:44,802 INFO Starting unattended upgrades script
2022-05-22 06:55:44,803 INFO Allowed origins are: o=Trisquel,a=nabia, o=Trisquel,a=nabia-security
2022-05-22 06:55:44,804 INFO Initial blacklist:
2022-05-22 06:55:44,804 INFO Initial whitelist (not strict):
2022-05-22 06:55:46,462 INFO No packages found that can be upgraded unattended and no pending auto-removals
Here is /etc/apt/apt.conf.d/50unattendened-upgrades:
// Automatically upgrade packages from these (origin:archive) pairs
//
// Note that in Ubuntu security updates may pull in new dependencies
// from non-security sources (e.g. chromium). By allowing the release
// pocket these get automatically pulled in.
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}";
"${distro_id}:${distro_codename}-security";
// Extended Security Maintenance; doesn't necessarily exist for
// every release and this system may not have it installed, but if
// available, the policy for updates is such that unattended-upgrades
// should also install from here by default.
// "${distro_id}:${distro_codename}-updates";
// "${distro_id}:${distro_codename}-proposed";
// "${distro_id}:${distro_codename}-backports";
};
// Python regular expressions, matching packages to exclude from upgrading
Unattended-Upgrade::Package-Blacklist {
// The following matches all packages starting with linux-
// "linux-";
// Use $ to explicitely define the end of a package name. Without
// the $, "libc6" would match all of them.
// "libc6$";
// "libc6-dev$";
// "libc6-i686$";
// Special characters need escaping
// "libstdc\+\+6$";
// The following matches packages like xen-system-amd64, xen-utils-4.1,
// xenstore-utils and libxenstore3.0
// "(lib)?xen(store)?";
// For more information about Python regular expressions, see
// https://docs.python.org/3/howto/regex.html
};
// This option controls whether the development release of Ubuntu will be
// upgraded automatically. Valid values are "true", "false", and "auto".
Unattended-Upgrade::DevRelease "auto";
// This option allows you to control if on a unclean dpkg exit
// unattended-upgrades will automatically run
// dpkg --force-confold --configure -a
// The default is true, to ensure updates keep getting installed
//Unattended-Upgrade::AutoFixInterruptedDpkg "true";
// Split the upgrade into the smallest possible chunks so that
// they can be interrupted with SIGTERM. This makes the upgrade
// a bit slower but it has the benefit that shutdown while a upgrade
// is running is possible (with a small delay)
//Unattended-Upgrade::MinimalSteps "true";
// Install all updates when the machine is shutting down
// instead of doing it in the background while the machine is running.
// This will (obviously) make shutdown slower.
// Unattended-upgrades increases logind's InhibitDelayMaxSec to 30s.
// This allows more time for unattended-upgrades to shut down gracefully
// or even install a few packages in InstallOnShutdown mode, but is still a
// big step back from the 30 minutes allowed for InstallOnShutdown previously.
// Users enabling InstallOnShutdown mode are advised to increase
// InhibitDelayMaxSec even further, possibly to 30 minutes.
//Unattended-Upgrade::InstallOnShutdown "false";
// Send email to this address for problems or packages upgrades
// If empty or unset then no email is sent, make sure that you
// have a working mail setup on your system. A package that provides
// 'mailx' must be installed. E.g. "name at domain"
//Unattended-Upgrade::Mail "";
// Set this value to one of:
// "always", "only-on-error" or "on-change"
// If this is not set, then any legacy MailOnlyOnError (boolean) value
// is used to chose between "only-on-error" and "on-change"
//Unattended-Upgrade::MailReport "on-change";
// Remove unused automatically installed kernel-related packages
// (kernel images, kernel headers and kernel version locked tools).
//Unattended-Upgrade::Remove-Unused-Kernel-Packages "true";
// Do automatic removal of newly unused dependencies after the upgrade
//Unattended-Upgrade::Remove-New-Unused-Dependencies "true";
// Do automatic removal of unused packages after the upgrade
// (equivalent to apt-get autoremove)
//Unattended-Upgrade::Remove-Unused-Dependencies "false";
// Automatically reboot *WITHOUT CONFIRMATION* if
// the file /var/run/reboot-required is found after the upgrade
//Unattended-Upgrade::Automatic-Reboot "false";
// Automatically reboot even if there are users currently logged in
// when Unattended-Upgrade::Automatic-Reboot is set to true
//Unattended-Upgrade::Automatic-Reboot-WithUsers "true";
// If automatic reboot is enabled and needed, reboot at the specific
// time instead of immediately
// Default: "now"
//Unattended-Upgrade::Automatic-Reboot-Time "02:00";
// Use apt bandwidth limit feature, this example limits the download
// speed to 70kb/sec
//Acquire::http::Dl-Limit "70";
// Enable logging to syslog. Default is False
// Unattended-Upgrade::SyslogEnable "false";
// Specify syslog facility. Default is daemon
// Unattended-Upgrade::SyslogFacility "daemon";
// Download and install upgrades only on AC power
// (i.e. skip or gracefully stop updates on battery)
// Unattended-Upgrade::OnlyOnACPower "true";
// Download and install upgrades only on non-metered connection
// (i.e. skip or gracefully stop updates on a metered connection)
// Unattended-Upgrade::Skip-Updates-On-Metered-Connections "true";
// Verbose logging
// Unattended-Upgrade::Verbose "false";
// Print debugging information both in unattended-upgrades and
// in unattended-upgrade-shutdown
// Unattended-Upgrade::Debug "false";
// Allow package downgrade if Pin-Priority exceeds 1000
// Unattended-Upgrade::Allow-downgrade "false";
Automatic updates IIRC are set for nabia-security/main repository by default, abrowser/icedove updates comes from the nabia-updates/main repository.
As it's targeted for "safe" updates that won't change the behavior with new features, mostly what you want on a server update.
On a related subject, there is a recent update for update-manager that was not showing notifications accordingly, please manually install it so the issue gets fixed, and following updates will be notified as they should.
This can be easily done on a terminal,
Ctrl + Alt + T
sudo apt update ; sudo apt upgrade
Done!
Regards.
ARk74 - many thanks for your help. I just ran sudo apt upgrade and my system is fully up to date.
I now have numerous new entries in Software & Updates, Other software. Only one item is checked and there are several duplicate entries. There is also an obsolete entry for the 8.0 CD which has been there for a long time.
Which items should be checked?
Thanks!
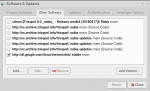
If you never want to download source codes, none of them.
- Login o registrati per inviare commenti

